![]()
A team led by researchers Charles Lim (background) and Zhang Gong (foreground) at the National University of Singapore have developed an optical power-limiter that could prevent certain kinds of bright-light attacks for eavesdropping on quantum-secured communications. [Image: CQT/NUS]
In theory, quantum cryptography enables two or more people to communicate with one another in complete secrecy. In practice, eavesdroppers can exploit weaknesses in the equipment used to send and receive secret keys.
Researchers in Singapore have now shown how practice can be brought closer to theory—by inserting a fairly simple passive device to prevent eavesdropping attacks involving bright light (Phys. Rev. X, doi: 10.1103/PRXQuantum.2.030304). They reckon their solution could be widely adopted in future, having shown that it can be applied to a number of popular cryptographic schemes.
QKD’s bright-light vulnerability
The power of quantum key distribution (QKD) stems from the fact that the secret keys used to encrypt and decrypt messages are encoded using the quantum properties of photons or other particles. This means that any eavesdropper—known conventionally as Eve—who’s trying to intercept the key on its way from the sender (Alice) to receiver (Bob) will reveal themselves through their act of quantum measurement.
However, QKD has an Achilles’ heel: its reliance on very weak pulses of light to encode data at the single-photon level. By exposing either the sending or receiving equipment to bright light, Eve can transform these devices into classical instruments—and therefore remove the quantum-enabled secrecy.
Power-limiting solution
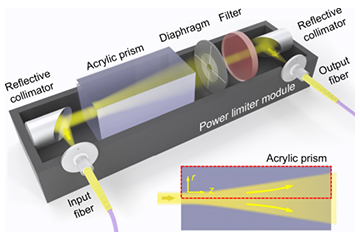
Schematic of power limiter designed by the Singapore group. [Image: G. Zhang et al., PRX Quantum, doi: 10.1103/PRXQuantum.2.030304; CC BY 4.0]
In their recent work, Charles Lim, Gong Zhang and colleagues at the National University of Singapore have developed a system to limit the optical power that such attacks rely on. Their device exploits an acrylic prism with a negative thermo-optical coefficient. Incoming light generates a gradient in temperature, and therefore in refractive-index, inside the prism that turns the acrylic into a concave lens. A small aperture placed behind the prism blocks most of the resulting diverged light beam, diminishing the beam power.
The researchers tested their idea by building the device using prisms with a variety of lengths and with a diaphragm that allowed them to vary the aperture. They found that in all cases the set-up introduced an upper limit on the output power, but that, as expected, longer prisms and smaller apertures yielded the lowest limits, with a roughly 10-cm-long prism and 25-μm-diameter aperture reducing the maximum power to about 1 μW.
The researchers found that the device works well even when dealing with signals of varying wavelength or pulse width, for example. They also showed that it preserved the quality of the signals, having very little impact on photons’ intensity, phase or polarization. They acknowledge that there is a trade-off between the (desired) reduction in optical power and (undesired) loss due to the device coupling, but say that this balance can be tailored for different applications.
Application to QKD schemes
Indeed, Lim and colleagues describe in some detail how the device could be employed in specific applications. One of these is centered on “measurement-device-independent QKD”, which involves both Alice and Bob generating key bits and sending them to a third (untrusted) party, Charlie. With Charlie merely registering whether or not the bits in each case match one another, rather than measuring their absolute values, Alice and Bob can generate a secret key without having to rely either on the integrity of the detector or on Charlie’s honesty.
The weakness of this approach is that Eve can still target the transmitters of Alice and Bob, and thereby carry out a “Trojan-horse attack” by bouncing bright light off either of the devices and using the reflections to gain information on the key bits. The answer, say the Singapore researchers, would be to insert a power limiter between each transmitter and Charlie’s detection equipment, thus reducing the rate at which Eve can siphon off photons, such that she no longer gains useful information.
Another application analyzed in the new work involves a more straightforward direct line of communication between Alice and Bob. In this case, Eve could potentially steal a key by using bright light to either damage or “blind” Bob’s receiver. The solution in this case would be to insert power limiters at the output of Alice’s transmitter and the input of Bob’s receiver.
Lim and colleagues reckon that their new device can ensure protection for a broad range of QKD protocols without having to modify pre-existing cryptographic equipment. Claiming that it would also be “compact, robust and cost-effective,” they argue that the power limiter has the potential to “become a standard tool for quantum cryptography applications.”
